[vc_row][vc_column skip_html=”yes”][text_block]
The Gist of the Mission
The bad news is that 100 percent cybersecurity is unattainable. The best we can do in the realm of cybersecurity is to build a portfolio of mechanisms that deliver the maximum protection of what is most important to us for the least amount of money and effort.
Portfolio theory in financial investment is concerned with optimizing the returns in a portfolio invested in different asset classes. This mission asks the question: How can we learn from the principles of financial portfolio theory and create an analogous theory of a balanced cybersecurity portfolio?
The initial work on this mission has been done in a series of articles listed at the end of this mission. The current state of the framework is shown in the following graphic:
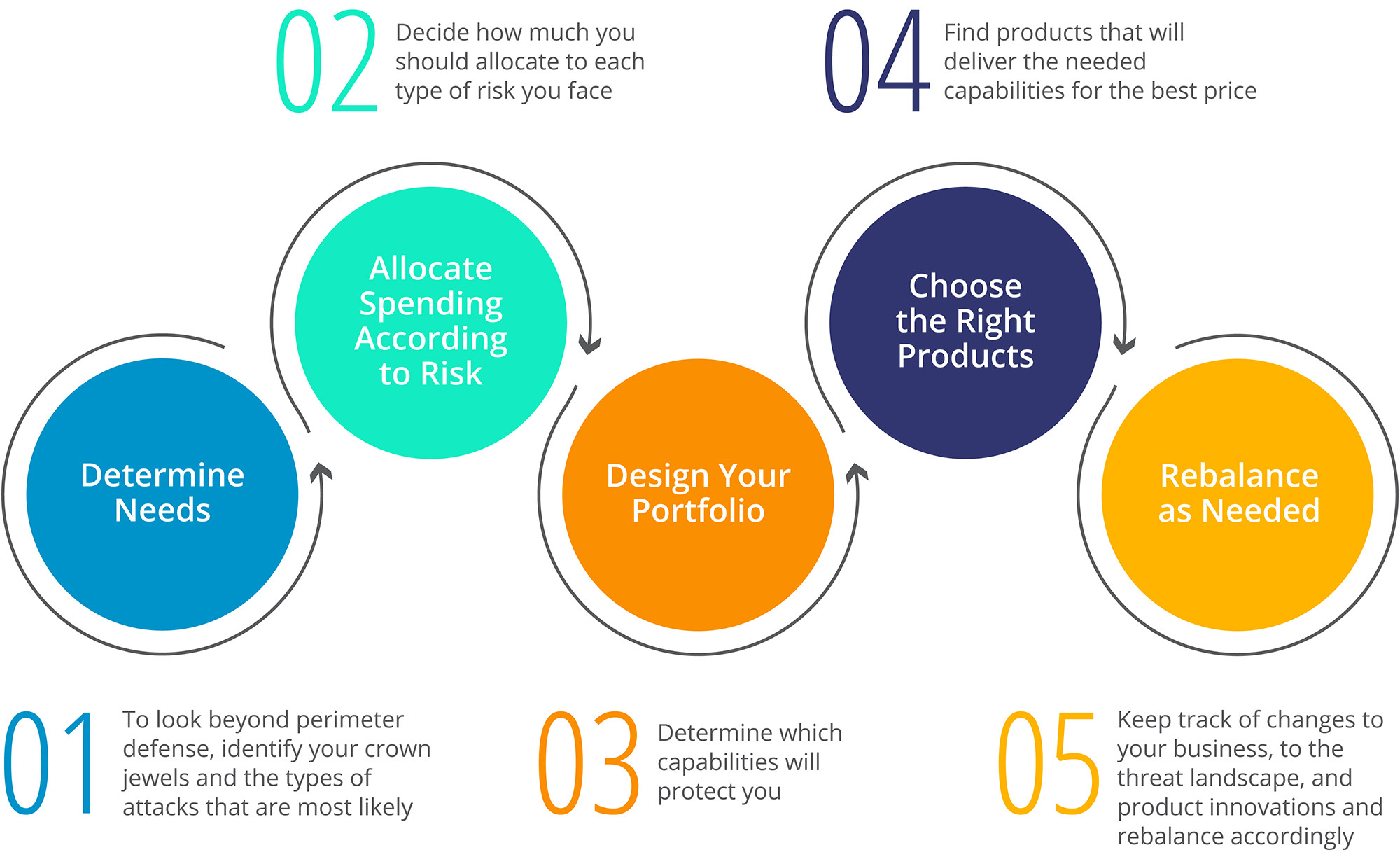
So far in this mission, we have written 25 stories (full list below) covering:
- Our emerging theory of a Balanced Cybersecurity Portfolio
- Commentary from vendors on the framework and how their products fit it
- General stories about cybersecurity topics
Read on to find out more about how we are answering the central questions for this mission. We are eager to collaborate with Early Adopters who share our passion for figuring this out.
The Mission
We’re entering a world of deepening complexity and far vaster breadth when it comes to security for the modern enterprise. With companies integrating legacy data centers, manufacturing facilities, and networks with the cloud and the Internet of Things (IoT), all connecting to an uncontrollable mass of independently governed endpoints, companies face a constant challenge of trying to decide what to protect and how to protect it.
The best approach to finding the right set of products and capabilities for your business is to adopt a portfolio approach. Similar to the way in which an individual invests in retirement savings by spreading their funds around, rather than putting all their money into one investment, companies have to find the right balance for their needs. What should that balance of products in a properly functioning portfolio provide?
When thinking about how companies should choose to spend their security dollars, a leading framework to use as a guide is that of the National Institute of Standards and Technology (NIST), although many security professionals also rely on ISO 27001. There are many others. The NIST framework offers five main functions companies need to be able to address in their approach to cybersecurity:
- Identify threats, including capabilities like asset management, risk management, and governance.
- Protect against them, including access control, maintenance, and data security.
- Detect them when they do occur, including monitoring and anomalous events.
- Respond to threats that get past your defenses, including response planning, communications, and mitigation.
- Recover from the hack, including communications taken in the wake of an attack, recovery planning, and improvements to systems and procedures.
(One result of our research so far is that we believe the NIST framework should be extended to include a Predict step.)
Building a Balanced Cybersecurity Portfolio
How much you need to invest in each of these categories is highly dependent on the unique needs and assets of your business. You want a portfolio that protects your “crown jewels” foremost — this is where your greatest investment should go. But since you do not have an infinite amount of money to spend, you then have to recognize the areas of cybersecurity where you can have enough protection to ward off would-be attackers. A key question is how to spread your limited dollars and resources over these categories to ensure your business is as protected as possible. Here are a few things to keep in mind.
No one is 100% safe: What’s crucial to recognize is that no cybersecurity portfolio can ward off all threats. Today, there are too many threats and too many sophisticated ways to get into a company’s network, to be 100% secure.
A security profile is not your only need: The NIST framework does provide some focus on portfolio analysis, including both the assets you need to be protected and the security used to protect them. The NIST framework, and other structures like it, help companies to organize a holistic approach to security. But it’s also important to remember that even with a strong security portfolio, there still needs to be security officers matching the needs of the business to the framework and available technologies. It is vital to remember that a fully realized vision for security must integrate people, process, and technology. We are assuming that the people and process aspects are being considered carefully in combination with an analysis of available technology.
A Process for Portfolio Design and Rebalancing
Based on our research so far, we have identified five key steps (described in the graphic above) that must be included in a company’s process as they build a cybersecurity portfolio:
- Determine needs: Look beyond perimeter defense and identify your crown jewels and the types of attacks you are most likely to face, and then aim the bulk of your resources there.
- Allocate spending according to risk: Decide how much you should spend on each type of risk you face.
- Design your portfolio: Determine which capabilities will protect you.
- Choose the right products: Find the products that will deliver the needed capabilities for the right price.
- Rebalance as needed: Managing a portfolio should be an ongoing process. Keep track of changes to your business and the larger industry landscape as well as product innovations and rebalance your portfolio accordingly.
Questions This Research Will Answer
Our research into building a cybersecurity portfolio continues to evolve. As it does, we seek to answer the following questions:
- Why is there now a need for a portfolio approach?
- What has changed to bring about this need?
- What guidance can be given and standardized to help in the formation of a portfolio?
- How can a company know that it’s covering all the bases?
- Since a company cannot prevent every attack and invest in 100% security, how does a company identify which capabilities it needs to ensure are at an A+ level and which ones it can work at a lower pass/fail level?
- What are the signs of a good and balanced portfolio?
- Why will portfolios be unique to each individual business?
- What are the signs that a portfolio is out of balance?
- What can the NIST framework teach us about creating a balanced portfolio?
- What are other cybersecurity frameworks useful to fashioning a solid portfolio?
Early Adopter Cybersecurity Research
Balanced Cybersecurity Portfolio Series
- How CISOs Can Create A Balanced Portfolio Of Cybersecurity Products
- How To Design Your Cybersecurity Portfolio
- How To Select The Right Products For Your Cybersecurity Portfolio
- Why It Is Always Time To Rebalance Your Cybersecurity Portfolio
Security Stories on Various Topics
- Does Cyber Security Have An Operational Excellence Problem?
- What Does Bugcrowd Tell Us About The Future Of Crowdsourcing?
- Infographic: The Anatomy of Cybersecurity
Vendor Specific Stories in the Balanced Cybersecurity Portfolio Series
- How To Find Cybersecurity Vulnerabilities Across Your Environment
- Extreme Cybersecurity Visibility: You Can’t Secure What You Can’t Measure
- Why You Must Build Cybersecurity Into Your Applications
- How To Protect Yourself From DDoS Attacks
- Keeping Threat Intelligence Ahead Of The Bad Guys
- 6 Ways Your Apps May Be Attacked: How Crowdsourced Penetration Testing Improves Software Development
- Why Understanding And Control Should Be Key Parts Of Your Cybersecurity Portfolio
- How To Stop Hackers By Thinking Just Like Them
- Visibility With A Human Touch: Splunk’s Take On Balancing Your Cybersecurity Portfolio
- Protection and Collaboration: How Foxit Extends Cybersecurity To PDFs
- Protect Four Key Areas To Create A Balanced Cybersecurity Portfolio
- BioCatch: A New Model For Continuous Security
- Addressing The Visibility Gap – How ForeScout Fits Into A Balanced Cybersecurity Profile
- How Complementary Cybersecurity Solutions Make Your Company Safer
- Why Thinking Like Your Enemy Is A Valuable Strategy For Your Cybersecurity Portfolio
- Why Prediction Should Be Added To The NIST Cybersecurity Framework
- How Data Protection Platforms Can Power A New Generation Of Apps, AI And Data Science
- An Ounce of Prevention – How CrowdStrike Fits Into A Balanced Cybersecurity Portfolio
General Cybersecurity Stories
- Turning The Lights On Inside of Amazon Web Services
- Does Your Company Need A Mobile Security Solution?
- Why Most IT Security Suffers From Unbalanced Spending
- How To Choose The Right Eyes and Ears for Cybersecurity
[/text_block][/vc_column][/vc_row]

