Active Defense: How Deception Has Changed Cybersecurity

The patterns of cyber attacks are well known and so are the targets. The bad guys are seeking to break in to get valuable data or take actions that benefit them, and want to go undetected for as long as possible. There are a number of solutions out there dedicated to prevention, system lock-down, prevention of lateral movement, and otherwise detecting anomalous behavior.
The challenge for detection, however, is how to do this faster and more comprehensively, with the highest chances of success, while minimizing operational overhead and false positives. That’s where the technique of deception, which is now being realized in a variety of products, is vitally important.
Deception is the evolution of something that used to be done externally to find nefarious actors, and it has its origins in the idea of the honey pot — external sites that would attract people who had bad intentions so that they could be identified. While honey pots were often used by security researchers, it was not a popular technique for enterprises. Deception essentially takes a new approach and moves threat deception inside the network, offering more valuable insight into threats that have penetrated perimeter defenses. And in doing so, it offers a way in which to generate only high-fidelity alerts and to arguably reduce the time to detect an attack dramatically.
With deception methods today, you pepper your internal infrastructure with seemingly available valuable decoys and information that should never be accessed by anyone legitimately. If someone accesses these assets, you know you have an intruder or at a minimum a policy violation that has created security risk. This detection mechanism is particularly valuable when the attacker is already inside the network, as in the case of insiders, trusted third-parties, suppliers, and contractors.
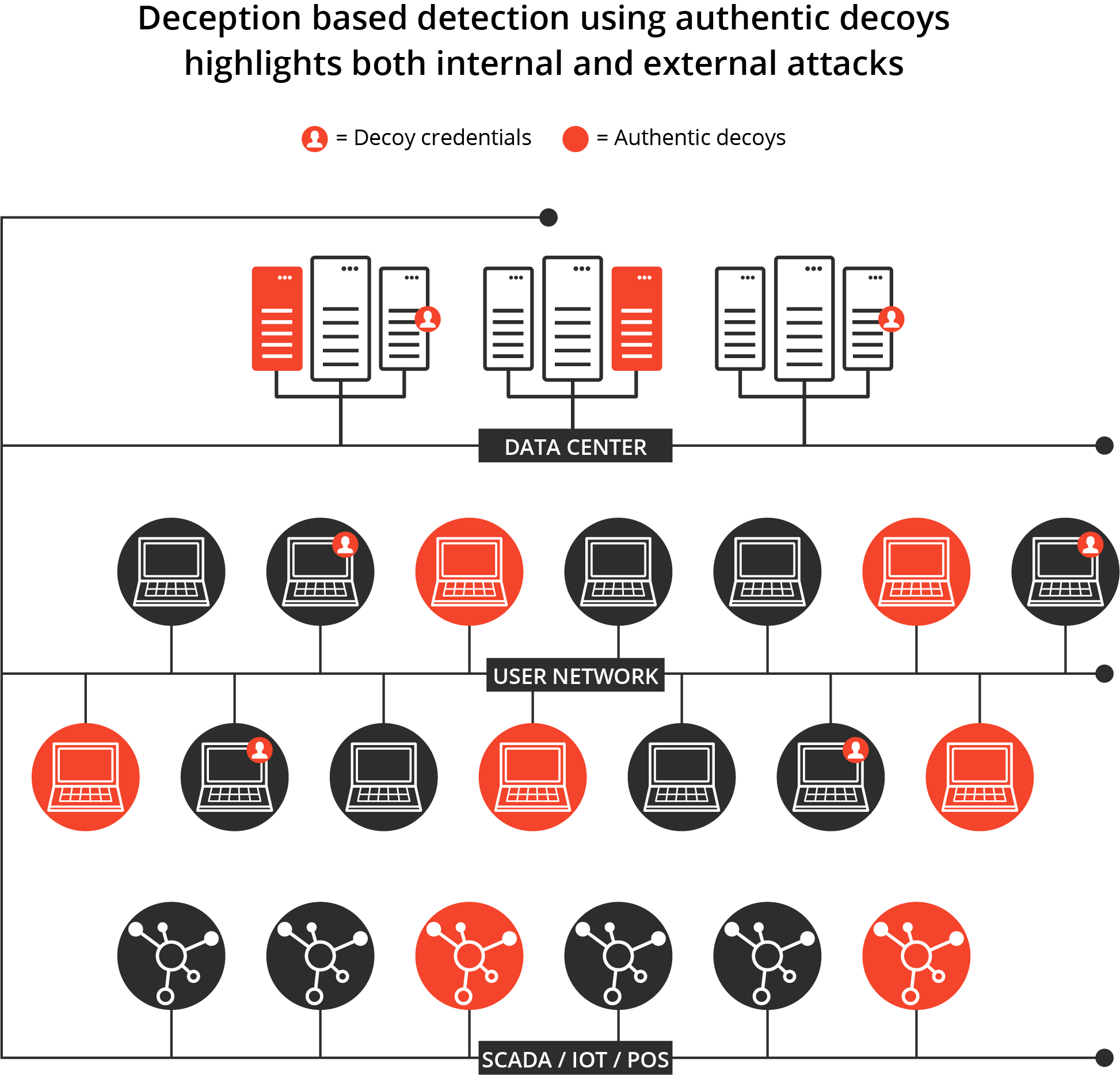
Deception inside a company is like those invisible laser beam tripwires that you see in movies about a big heist. When anyone attempts to access those internal decoys or deception credentials, the digital equivalent of a laser sensor is triggered and you know you’re under attack. You also know where inside your network the attack is coming from and how the attacker is attempting to violate your systems. You can then detect the attack as soon as it attempts to spread, whether this be via credential theft or reconnaissance.

Carolyn Crandall, Chief Deception Officer, Attivo Networks, Inc.
Once the attack has been detected, countermeasures can begin. The behavior of the bad actor can be immediately shut down, or the bad actor can be observed. By watching what they do, it may be possible to gain more information about who is attacking and what they are attempting to do. Advanced forensics data can then be automatically compiled, aiding security teams in not only detecting, but also in threat hunting and the eradication of threats. Deception can be an important way to engage in what is being called active defense. In military terms, an active defense is defined as “The employment of limited offensive action and counterattacks to deny a contested area or position to the enemy.” These actions are designed with the intent to change the asymmetry of an attack and to increase the cost to cyber-adversaries.
We’re going to take a look at the nature of deception security products initially by looking at Attivo Networks. Later, I’ll examine other products, which take different approaches to implementing deception. For this blog, I spoke with Carolyn Crandall, Chief Deception Officer and Chief Marketing Officer at Attivo.
Deception and a balanced framework for cybersecurity
Deception is a technique that fits into our balanced cybersecurity framework as part of the detection category as defined by NIST. We developed our framework in our research mission and extended it at this year’s RSA conference by asking some crucial questions: what are the cybersecurity gaps, how can new components be integrated, how can a data warehouse be added to help future proof a portfolio, and how more business benefits can be derived from the portfolio.
But it’s also important to understand that as we move forward with the balanced portfolio approach and it becomes more mature, one of the key aspects of increasing maturity is to capture and standardize the work that analysts do. This is crucial so analysis of a cybersecurity incident isn’t trapped inside a personal spreadsheet or document of an individual analyst, but is part of a playbook that can be shared and learned from. This will help not only detect attacks, but prevent them, and lead to the ability of creating automated, coordinated responses to attacks.
Traditional cybersecurity is built on silos.
“Traditional cybersecurity is built on silos,” said Crandall. “But as we’ve looked at the model today, it’s not all about prevention. You’ve got prevention, detection, response, and many people even go into the area of prediction. And in order to get those things to work together, you need to be able to share information, automate processes, and retain the information so that it can be reused, potentially using repeatable playbooks.”
Ultimately, if companies are able to do this, the portfolio will be able to add value to the business, including a deeper understanding of the business operations, such as identifying crucial events, or providing detailed models of activity. If we move from a balanced portfolio to higher levels of maturity, we can also adopt a holistic medicine approach to cybersecurity. In this approach, instead of treating cybersecurity events as pathologies, we look at the business as a whole and ensure the business’ fundamental mission can be pursued in a safe way. The entire health of the business is supported in this way.
“With deception, there can be a tremendous amount of information accumulation, attack analysis, and correlation required to ensure the attack is stopped, purged, and prevented from returning. Internal information sharing between security controls empowers you to be more effective within your own organization and to build a stronger security defense. And then there’s the broader view of sharing attack information across industries or more widely so that everybody can benefit from that information and knowledge,” said Crandall.
What makes deception work?
For deception to work, you must present what appears as reality to the opponent, by attempting to trick them into engaging with deception decoys or lures, which allows you to learn that they are inside your systems and also about how they are executing the attack. Obviously, this is an ancient concept used in all facets of business and life. But we’re focusing on how that general concept gets properly implemented in the cybersecurity realm.
It starts by putting in a bunch of tripwires. In order for these to work, you must be able to offer a view of reality that seems real and is attractive to the opponent. If you offer decoys or targets that seem fake, the attacker will avoid them and as such, the solution will not work. Deception must be authentic and attractive. That means real operating systems and credentials that look the same as the production environment.
For deception to be effective, first and foremost it needs to be authentic.
“For deception to be effective, first and foremost it needs to be authentic,” said Crandall. Attackers are sophisticated. To fool them, deception needs to be identical to production assets and credentials. It needs to be believable enough for them to fall for it.”
In addition, to bringing deception to its full power, it must be comprehensive and cover an ever-changing attack surface. Some vendors that provide deception-based cybersecurity only focus on one form of deception — like credentials, decoys, or data files. But it’s better if you can cover all attack methods and services by putting in credential and mapped drive objects to attract engagement and decoys to attack in the network, in the cloud, and in specialized places like the IoT, POS, and SWIFT. With today’s virtualized technology, you can make these deceptions ubiquitous, which gives you the highest probability of detecting an attack wherever it occurs. In the modern world, where attacks are often polymorphic, this can be especially useful.
The deception must also be scalable. Deception is more efficient than other means of detecting cybersecurity threats. You’re not looking at every piece of data trying to determine normal and then detecting anomalies. Rather, with deception, you’re putting in decoys or bait and if those are accessed, you know there’s a problem. There are no false positives.
Scalability is thus not about processing power, but about designing and implementing a comprehensive authentic set of decoys that can then be put in place throughout your environment. Once those decoys are deployed, you must then be able to manage and refresh them periodically to maintain authenticity. The automation of deployment and response is the real key to scalability and easy ongoing operations.
Deception is also unique in that an organization can safely, in a deception sandbox, engage attackers for deeper forensics. Security analysts can observe attackers in a much safer manner than other forms of detection because the assets under attack are decoys. In a normal attack, analysts want to stop the attack immediately from accessing a valuable asset. With deception, you can engage an attacker and then activate countermeasures. This is perhaps the most unique aspect of deception, as it changes the balance of power between attackers and defenders, and you learn more about them than you would have otherwise. The changing of the asymmetry of the attack will at minimum slow the attack and increase attacker costs. In some cases, this could also serve as a deterrent, driving the attacker to find an easier target.
When you prevent an attack, you don’t get the opportunity to study it. When you just block it, you stop it from coming in, but you’re not learning from it.
“Part of the fundamental problem is when you prevent an attack, you don’t get the opportunity to study it,” said Crandall. “When you just block it, you stop it from coming in, but you’re not learning from it. Valuable information is lost, information that can be critical to quickly eradicating the attack and preventing the attack from returning.”
Why do we need a flexible suite of deception?
We need a flexible suite of deception because we want to be able to put sensors in any part of the IT real estate that might be attacked and to promote the early detection of all attack methods. You can argue that most of the time that attackers are going after data or credentials, but in the modern world, they’re really going after anything of value that they can exploit, including computing resources that can be used to mine cryptocurrency or run botnets. As Mark Urhmacher has pointed out, “The idea that you want to be the second slowest zebra in the herd is no longer relevant — the lions are now smarter. Attackers are now using AI to attack all the zebras at once.”
What type of activities do deception systems detect?
State of the art deception systems detect a wide variety of threats and are not reliant on known signatures, database look up, or pattern matching:
| Credential Theft | When somebody tries to attack and lift username and passwords from OLAP directories or other places they are stored. |
| Lateral movement | When someone in one part of network tries to access other parts of the network that are off limits to them. |
| Attacks on directory systems | These can be directories of users or file directories. |
| Man-in-the-middle | These are attacks where a hacker intercepts and possible changes communication between two parties who do not know their exchanges have been infiltrated. |
| Sensitive data | This is sensitive, high-value data. |
| Geo-fencing | The attacker steals planted deception files that when opened provide geo-location data and intelligence on targeted files. |
| Detecting attacks on data distributed outside your organization | It is often possible, using decoy docs, to put essentially GPS trackers on your data to see when it’s been accessed even after it has left your system. |
What are the benefits of using deception?
There are many benefits to using deception. Foremost amongst these is that it reduces dwell time and the mean time to detection and remediation. Additionally, through engagement, it provides deeper forensics of adversary intelligence including indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs). It is also not reliant on knowing every attack vector or method and is designed to detect early reconnaissance, credential theft, and lateral movement. Additionally, as soon as you recognize there’s a new place to be attacked, you can easily and in some cases automatically put decoys around these new at-risk critical assets.
We set traps, lures, bait for the attackers inside the network.
Deception-based cybersecurity technology like Attivo allows companies to gain internal threat visibility where before they had none. “We set traps, lures, bait for the attackers inside the network and I would say one of the biggest myths about that is that this is a technology that you would want to do last, versus doing earlier on,” said Crandall. “Whether you have the most sophisticated security controls, or maybe you don’t, you need to know as quickly as possible about the threats that are inside your network and whether they can cause you harm. It’s valuable for both large and small companies, sophisticated and unsophisticated, to get that canary in a coal mine, to know when you have something bad happening.”
Attivo’s technology implements a full stack of deception in order to achieve all these benefits. It reduces dwell times of attacks by setting up decoys, traps, and bait for attackers. Its native partner integrations with a wide variety of other cybersecurity products ensure that as much information as possible can be automatically shared when an attack occurs and that traditional knowledge silos are removed. With Attivo’s system, knowledge about an attack is gathered safely within its built-in sandbox and its attack visualization tools can help an organization quickly gain actionable threat intelligence. It also allows companies to learn from attacks to create automated response processes and repeatable playbooks to shut down current attacks and to prevent or detect future attacks.
Attivo enhances endpoint security by planting deception credentials and then closely monitors and captures information on people trying to use this login information. Their endpoint solution will also provide maps of likely attack paths in order to quickly understand how an attacker would move to get to target assets and if there are exposed or misconfigured credentials that would facilitate them quickly doing so. Of particular interest is they way they map deceptive network shares at the endpoint to address ransomware attacks by using high-interaction deception to occupy the malware and delay it from spreading, buying time for incident responders to eradicate the infection before it causes more harm.
The value in using deception to change the asymmetry of the attack becomes very evident when using it in conjunction with a security test, in a Red/Blue exercise or as part of a penetration test. As a realistic test of attacker versus defender, such tests are valuable in their own right to validate security solutions and procedures. Adding deception gives the defenders an advantage they did not have before, and a capability to detect the attackers once they get inside the network as an additional line of detection. Deception can be used to not only detect the testers as they bypass other perimeter defenses, but also to validate the penetration test results because the detections act as an unofficial audit trail of the pentester’s activities.
Ultimately, as I mentioned earlier, deception provides a way of changing the balance of power between the attacker and the defender. The attacker, in the past, has had the power — they only had to succeed once, while the defender had to succeed all the time. Now, with deception, the defender can quickly detect the attack, learn the attacker’s tactics, and create an offensive playbook of countermeasures to outsmart their adversary. Attack analysis and forensics become far more actionable and powerful and high-fidelity alerts empower the automation of incident response actions such as blocking, quarantining and threat hunting.
It’s not enough to detect alone.You need to be able to take action on [the attack].
“It’s not enough to detect alone,” said Crandall. “You need to be able to take action on it, understand the attack, run the forensics on the attack, and then respond to it. Block it, quarantine, threat hunt it, build a better defense for the future. That’s all part of active defense. So detect early, reduce your dwell time, and improve your time to respond or time to react.”







Leave a Comment